BIG DATA AND SECURITY
By TheWAY - 3월 24, 2018
BIG DATA AND SECURITY
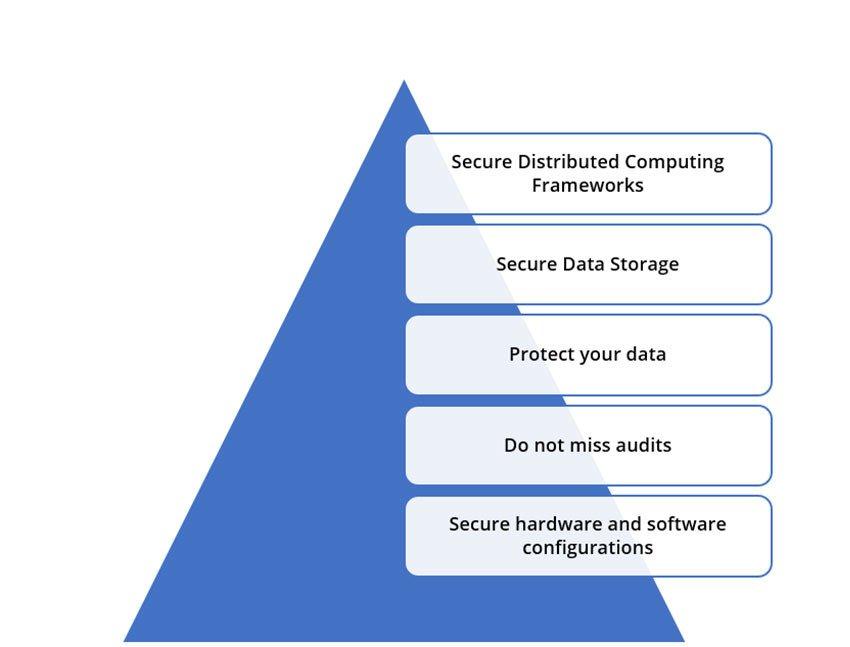
Big data exhibits the 4 V's (volume, variety, velocity, veracity). are innumerable, ranging from banking, healthcare, insurance, pension, and governmental proceedings, due to its numerous advantages. Every chunk of data in an organisation is crucial, and it is important to manage it securely. Big data security is one of the major concerns faced by any sector today, leading organisations into using more scalable tools to meet the security constraints




2 개의 댓글
Digital marketing is the component of marketing that utilizes internet and online based digital technologies such as desktop computers, mobile phones and other digital media and platforms to promote products and services.
답글삭제Digital Marketing Training in Hyderabad
Digital Marketing Course in Hyderabad
Amazon web services Training in Hyderabad.Amazon Web Services is a subsidiary of Amazon providing on-demand cloud computing platforms and APIs to individuals, companies, and governments, on a metered pay-as-you-go basis. The AWS technology is implemented at server farms throughout the world, and maintained by the Amazon subsidiary.
답글삭제